There’s been a recent rise in the number of ‘sextortion’ emails hitting inboxes lately, and while these type of scams have been around for a while now they are getting more sophisticated and aggressive.
What is a sextortion scam?
Sextortion is a word made by combining ‘sex’ and ‘extortion’ and is used by the IT industry to describe a type of blackmail or ransom, usually received via email.
The email usually scares the user by claiming that they have somehow managed to infect their computer and have records of them visiting adult sites and videos of them.
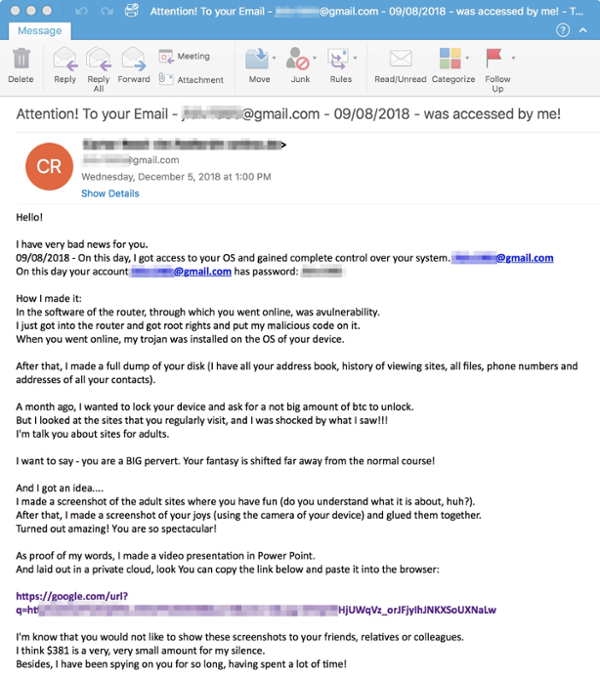 |
| An example of a 'sextortion' email currently circulating |
After scaring the victim, the cybercriminal threatens to expose them to family, friends or their employer if they do not pay a ransom.
How do sextortion scams work?
They criminal always claims to have infected the victim’s computer and either has browsing history or video evidence of them visiting adult sites.
Like all scams, the scammers use the power of social engineering to make their victim panic and before stopping and thinking logically, they have followed their instructions.
The classic sextortion scam will normally demand money and provide a way a way of paying, but there have been and influx of these emails that are providing ‘proof’ of their claims. The URL they provide however, will download and install either malware or ransomware on the victim’s computer.
What to do if you receive a sextortion email
Remember don’t panic! These emails are scams and are designed to induce panic and make you do something you will regret down the track.
Make sure you know how to identify scam emails and always be looking for red flags in your emails.
We recommend implementing cyber security training for all staff members to ensure they have the skills and knowledge to spot these emails. Employees are your last line of defence against these kind of attacks so make sure they have been trained and tested regularly.






Let Us Know What You Thought about this Post.
Put your Comment Below.